In reflecting on the relationship between IT careers and the foundational concepts of information technology covered in TEC 101, it becomes clear that understanding these basic principles is crucial for anyone pursuing a career in IT. As a student, I see that the knowledge gained from learning about the history of computers, computer science, hardware components, programming languages, application software, database management, and network architecture is essential for building a successful IT career. By linking these theoretical concepts to real-world IT practices, I can better understand how my studies prepare me to contribute effectively to the fast-changing world of information technology.
To start, the history of computers and the basics of
computer science are fundamental to IT careers. Knowing how computers have
evolved over time helps IT professionals understand how current technologies
came to be and where they might go in the future. For example, early computers
like the ENIAC laid the groundwork for the modern systems we use today. This
historical knowledge allows IT professionals to adapt to new technologies and
anticipate future trends (Ceruzzi, 2021). Additionally, understanding how
computers operate—how they process data and interact with hardware—helps IT
professionals manage and optimize systems in roles like system administration,
network management, and software development (Vahid & Lysecky, 2019).
Next, IT professionals heavily rely on major hardware
components to do their jobs. The central processing unit (CPU), random access
memory (RAM), storage devices, and networking hardware are all essential parts
of a computer system. IT careers often involve maintaining and upgrading these
components to ensure that systems run smoothly. For example, an IT professional
might need to diagnose a hardware issue or improve a system's performance by
upgrading its components. Understanding how these parts work together is key to
making informed decisions and keeping systems efficient (Vahid & Lysecky,
2019).
Programming languages and how programs are executed on a
computer are also crucial aspects of IT careers. IT professionals often use
programming languages like Python, Java, and C++ to develop software, automate
tasks, and manage systems. These languages are essential tools for solving
problems and innovating in fields like software development, data analysis, and
cybersecurity (W3Schools, 2023). Moreover, knowing how programs are executed,
including compiling code and debugging, ensures that software runs efficiently
and without errors (Vahid & Lysecky, 2019).
Application software plays a significant role in IT careers
as well. IT professionals use various software tools to perform their tasks,
from database management systems to network monitoring tools. Being proficient
in these applications allows IT professionals to work more effectively and
contribute to their organizations' success. For example, a database
administrator needs to know how to use database software to store, retrieve,
and secure information, while a network administrator might use software to monitor
and manage network traffic (Vahid & Lysecky, 2019).
Another important area is database management. Databases are
critical for organizing and retrieving information, and IT careers often
involve managing and securing these databases. IT professionals need to
understand how to use database management systems (DBMS) like MySQL or Oracle
to ensure data integrity, optimize performance, and protect sensitive
information. This knowledge is essential for maintaining the accuracy and
security of data within an organization (Vahid & Lysecky, 2019).
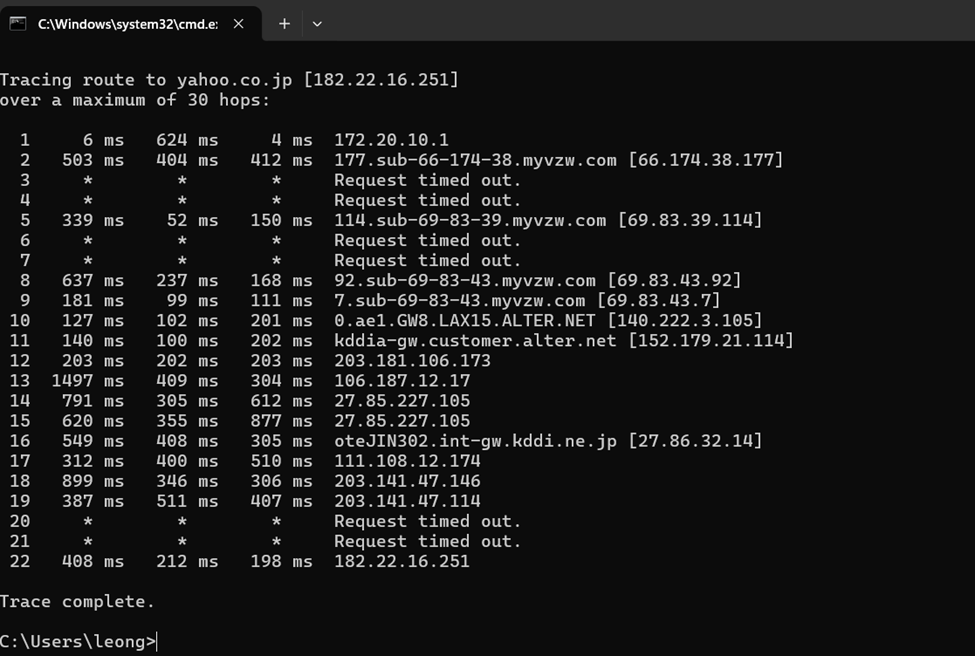
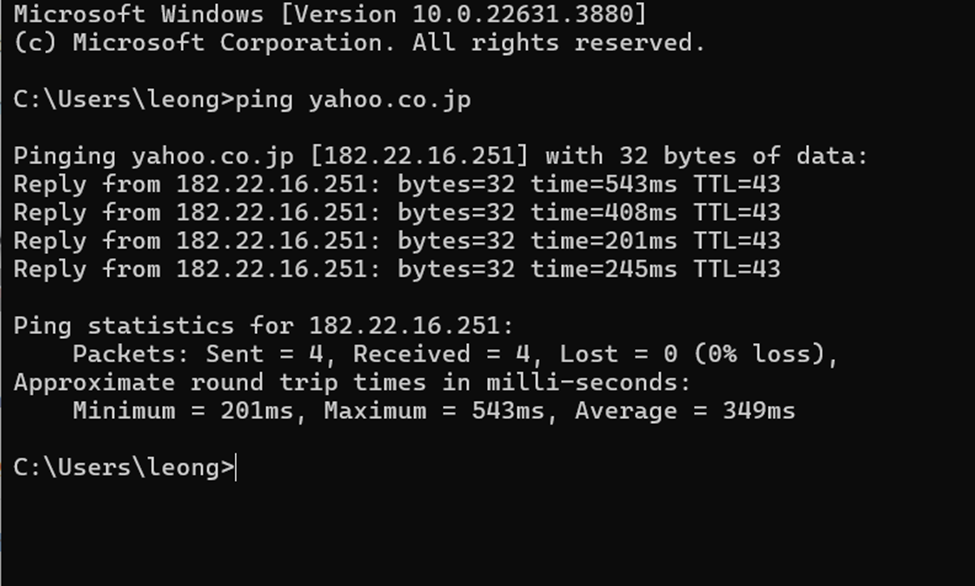
Finally, network architecture, management, and security are
central to many IT careers. IT professionals need to understand how to design,
implement, and manage networks to ensure reliable communication and data
protection. This includes knowledge of network protocols, routing, switching,
and security measures. These skills are crucial for roles in network
administration, cybersecurity, and IT infrastructure management, where
maintaining a secure and efficient network is a top priority (Vahid & Lysecky,
2019).
IT careers are deeply connected to the fundamentals of
information technology. By mastering the basics of computer history, hardware
components, programming, application software, database management, and network
security, IT professionals are well-prepared to handle the challenges and
opportunities in the field. This strong foundation allows them to adapt to new
technologies, solve complex problems, and contribute meaningfully to their
organizations.
References
Ceruzzi, P. (2021). A History of Modern Computing (2nd ed.).
The MIT Press. Retrieved from
https://mitpress.mit.edu/9780262532037/a-history-of-modern-computing/
Vahid, F., & Lysecky, S. (2019). Computing Technology
for All. Retrieved from
https://learn.zybooks.com/zybook/TEC101:Fundamentals_of_Information_Technology&Literacy(TED2432A)
W3Schools. (2023). Introduction to Programming Languages.
Retrieved from
https://www.w3schools.com/whatis/whatis_programming_languages.asp